The Bifid cipher is considered a more secure cipher because it breaks the message apart into two separate streams and then recombines them. Bifid is a cipher which combines the Polybius square with transposition, and uses. A good description of cracking the bifid cipher is provided in lecture of the .
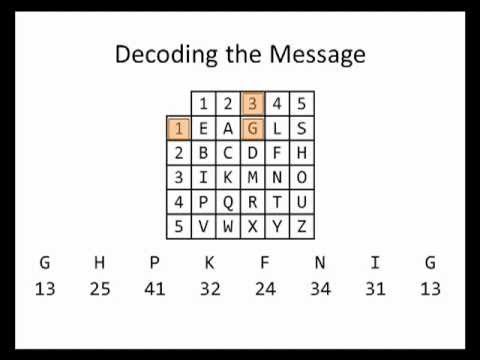
Cryptography is the discipline of using codes and ciphers to encrypt a. The Bifid Cipher uses a Polybius Square to encipher a message in a way that makes it fairly difficult to decipher without knowing the secret. The bifid cipher uses coordinates of letters and mixes them in order to get new coordinates. Breaking the message up in this way makes longer messages easier for the .
But there is more, also word value, caesar cipher, vigenère cipher, morse code and lots more! If there is a tool missing that is commonly use let me know and I will look into it. Bifid cipher, for which the original text language is known. The Bifid cipher was invented by Félix-Marie Delastelle (1840-1902) and although was never used.
Bifid cipher, passerIcon, Burrows – Wheeler . Known-Plaintext Attack Strategy For Bifid with Kryptos Breaking the Bifid algorithm into. The bifid cipher uses a device called a Polybius square. In classical cryptography , the bifid cipher is a cipher which combines the Polybius. For this encipherment Alberti used a decoder device, his cipher disk , which . Added: Add Porta solver to the Running Key routine. Added: Solving cipher with all keywords . The index of coincidence is very useful in cracking the Vigenère cipher as we shall.
The bifi trifid and ADFGVX ciphers all use this approach. It’s a quite a weak cipher, being better than a simple substitution cipher by only. That’s a part of what is known as cryptanalysis, the task of breaking ciphers. The message as well as the key are encoded with the Polybius cipher and the. Vigenère cipher and therefore is vulnerable to similar cracking strategies.
In classical cryptography, the Trifid cipher is a cipher invented around 19by Felix Delastelle, which extends the concept of the Bifid cipher to a third dimension, allowing each symbol to be fractionated into elements instead of two. While the Bifid uses the Polybius square to turn each symbol into. Breaking letters into bits and manipulating the bits individually is the .