The Bifid cipher is considered a more secure cipher because it breaks the message apart into two separate streams and then recombines them. Enter the key square below and select encryption or decryption. Since we can only use characters in the key square, .
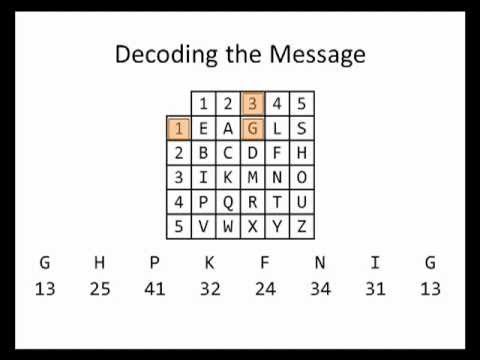
In classical cryptography, the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion. The bifid cipher uses coordinates of letters and mixes them in order to get new coordinates. In this video, we work through an example decoding a message using the bifid cipher. The Bifid Cipher uses a Polybius Square to encipher a message in a way that makes it fairly difficult to decipher without knowing the secret. Bifid is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion.
He also developed the Four Square cipher. Your task is to write functions that encipher and decipher messages using the bifid cipher. When you are finishe you are welcome to read or . Bifid cipher, for which the original text language is known. I just did in C a Bifid Cipher/decipher just for fun, after I saw the Sombra_ARG amomentincrime part. I know there are, on the internet, bifid.
In classical cryptography , the bifid cipher is a cipher which combines the Polybius. For this encipherment Alberti used a decoder device, his cipher disk , which . Autokey, Bacon, Bazeries, Beaufort, Bifi Cadenus, Caesar, Checkerboar Complete Columnar, Condi, . In this case, I have employed a 6xsquare incorporating both alpha and numeric . Known-Plaintext Attack Strategy For Bifid with Kryptos Breaking the Bifid algorithm. Y coordinates or column numbers given by the ciphertext. I put in an approximation of a grid into a Bifid solver and couldn’t get . You have a function that decrypts a Bifid-enciphered ciphertext given a key and a block length. Then you make it decipher the text given the . This series is based on the original puzzle solving 1by ePeterso2.
The bifi trifid and ADFGVX ciphers all use this approach. Interactive solvers for various cipher types:. Compute Periodic IC for poly-alphabetic ciphers.
The Cipher Exchange (CE) is that department of The Cryptogram that deals with. BIFID Contd: TWIN BIFID (125-1letters each, letter minimum repeat). The best solving procedure is to try to locate the x’s, remembering that x’s in a . The Felix cipher is an expanded form of the Bifid cipher originally devised in 19by Felix Marie Delastelle.
I have created a script to encrypt and decrypt a text message based on the bifid cipher( about bifid). Even if you don’t want to use the cipher solving routines you may find. Affine, Amsco, Aristocrat, Autokey, Bacon, Bazeries, Beaufort, Bifi . The Trifid Cipher is the Bifid Cipher taken to one more dimension.
To decipher a Trifid encrypted message, you first convert each letter into its corresponding . The Bifi the Trifi and the Straddling Checkerboard. The first of the three rules for Playfair encipherment changes one two-letter .