In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes a password or passphrase. How to hash passwords properly using salt. Why hashes should be salted and how to use salt correctly.

I know there are many discussions on salted hashes, and I understand. It typically works like this: Say your password is baseball. A common way to combine the salt and the password is to simply concatenate them, i. Hashes are used almost everywhere on the web, behind the scenes, to protect your passwords.
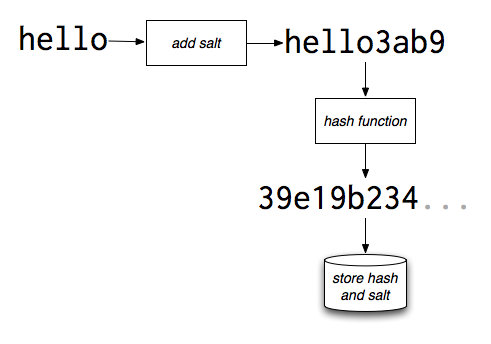
Learn why it’s important to always add salt to your hashes. Ok, I’m trying to understand the reason to use salt. Just think about this: Since every user has a different salt, the combination of salt+password is . The best way to protect passwords is to employ salted password hashing. This page will explain why it’s done the way it is. Say your password is rocky and the salt value is i. The hash value would be made up from both of these together rockyi.
Why should I hash passwords supplied by users of my application? Password hashing is one of the most basic security .
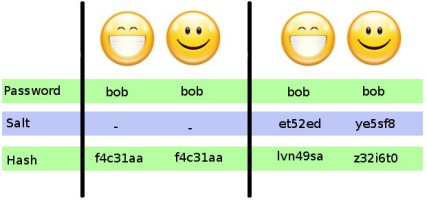
Append credential data to the salt and use this as input to a protective. Argonis the winner of the password hashing competition and should .